"Gone off the screen and started pumping information": New information on Hamas's malicious app
The ISA and the UN have revealed that in Hamas they tried to persuade soldiers to download a malicious app for a smartphone, which it could then take over. At Security Point, Check Point investigated the app and its source of attackers, and discovered new findings that shed light on the sophisticated attack
"Gone off the screen and started pumping information": New information on Hamas's malicious app
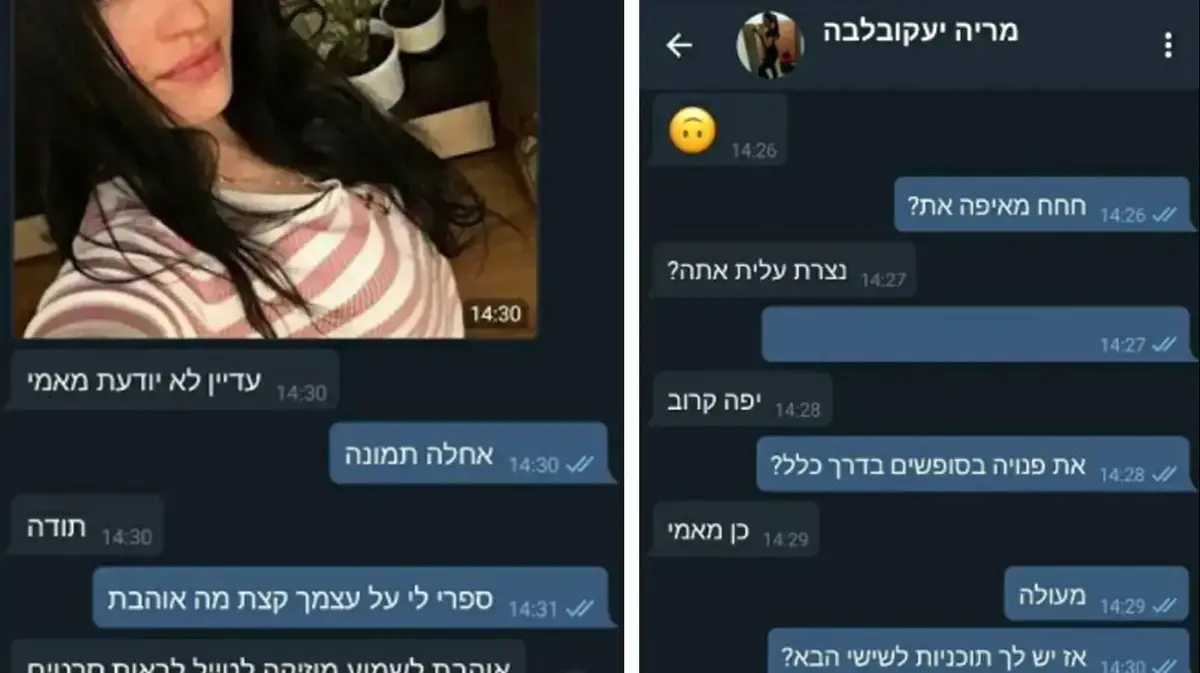
Photo: Duetz, editor: Tal ResnikShabak and artist revealed Sunday that phones of hundreds of regular soldiers and junior officers have been infected with malicious software in recent months. Hamas through fake social networking profiles. In an effort to complete the full picture, Check Point's Mobile Research Unit investigated its malicious applications Hamas used the operation, and in this context, examined the attack servers used by Hamas to gather information from IDF soldiers.
More in Walla! NEWS More in Walla! NEWS"Noa Danon" app appeals: That's how Hamas tried to break into Israeli soldiers' phones
To the full articleCheckpoint researchers found that after the soldiers received links to download the app and reached a fake site, when the app was downloaded, it displayed an error message - "The device is not supported" and then the icon appears to have been deleted from the screen, giving the app a sense of being removed. But in practice, it is installed on a smartphone and starts using the permissions it requests during the installation phase and with all the capabilities such as: picking up the user's location, receiving the message content, opening a microphone and camera, and even recording calls.
More in Walla! NEWS
"What, is it paying for people to come?": The network laughs at the interview with Nicole Raidman Corona virus also threatens shipments: So make sure you get your packages Will Apple launch a discounted version of AirPods Pro headphones? Glasses Remover - with free testing and lifetime warranty promoted contentDisappeared from the screen, but began to act in the background. (Photo: PR)
Hamas Application Permissions (Photo: PR, PR)
The same group that carried out the attack is called "aptc-23," a well-known group that is affiliated with Hamas and operates in Israel in a similar way. Check Point previously found that the group was working against the PA, with its spyware being able to transfer materials from the computers, with emphasis on Word files, PDFs, tables and more. They also found that in the current attack, one server was used to attack and store the material, while also revealing that the group was using internal operating names such as: Jim Morrison (Doors soloist), Eliza Doolittle, Gretchen Blailer (American athlete) and other celebrities.