The Zoom app has become more and more popular as a result of the Corona crisis, and Check Point identifies a leap in phishing attempts through phishing sites
Zoom app
Fitness classes, distance learning, meetings, and social gatherings: While most industries are bleeding, there are those who benefit from the spread of the corona virus; The Zoom app has become one of the icons of the era and is home to millions of people. However, hackers are also trying to take advantage of the situation due to the growing use of the app.
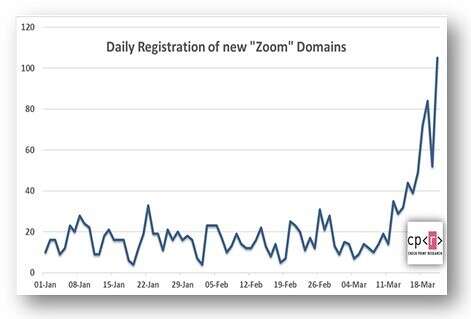
According to data security firm Check Point, there has recently been an increase in domain name registration including the word zoom (ZOOM), and at the same time an increase in the number of suspected sites that contain damage and impersonate an app install file. Running these files leads to the installation of InstallCore PUA, a file that could lead to additional malware installation.
The company has identified 1,700 new domains that have been set up around the Corona events and use the word zoom (ZOOM), and 25 percent of them have registered in the past week. Of these listed domains, 4 percent were found to contain suspicious properties, along with those posing as popular platforms such as Google Classroom and Google Hangouts.
How can you defend? The security company has provided a number of tips to help you not to fall into the trash.
1. Beware of emails and files received from senders you don't know, especially if they offer special offers or discounts.
2. Don't open unknown attachments or click links in the emails.
3. Beware of domains that contain misspellings
4. Make sure you order products from authentic sources. One way to do this is not to click on promotional links in emails
5. Make sure you have protection systems that address all network connections to prevent new attacks